Password is a secret word that is used for authentication or proves your identity, password is a foundation of security for most computer or computer networks. Usually a normal user do not know the importance of password, many users choose the simplest
password such as a pet’s name to help them remember it.
password such as a pet’s name to help them remember it.
Nowadays, many services use cryptography technique to secure their information, cryptography is the art of secret communication, by using cryptography techniques you can secure your password and make your password difficult to crack.
There is a different techniques to crack passwords below are the example of different techniques.
Guessing
This is an old but simplest method that an attacker used to crack passwords, as i told earlier that a normal user do not know the importance of password and a normal user do not care about passwords, many of the people use very weak passwords such as their pet’s name, lover name, friend or relative, phone numbers or passport numbers etc.
If your password is so weak than an attacker who knows you personally can easily guess your password, so be careful while choosing your passwords. If an attacker does not you personally so he/she uses some of social engineering technique to get your personal information.
If your password is so weak than an attacker who knows you personally can easily guess your password, so be careful while choosing your passwords. If an attacker does not you personally so he/she uses some of social engineering technique to get your personal information.
Dictionary Based Attack
Dictionary attack happen when an attacker create a wordlist(a dictionary) which contains some commonly used passwords, name of places, common names, and other commonly used words. To avoid this type of attack you must choose a strong password.
There is various password cracking tools present on the internet like:
There is various password cracking tools present on the internet like:
● Cain & able
● John the Ripper
● THC hydra
● Aircrack (WEP/WPA cracking tool)
● L0phtcrack
● Brutus
● Or more.
● John the Ripper
● THC hydra
● Aircrack (WEP/WPA cracking tool)
● L0phtcrack
● Brutus
● Or more.
THC hydra
THC hydra is a network authentication cracker which supports many different services, click here for more information.
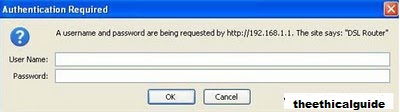
When you will get this screen that ask you to enter the password, if an attacker is not the authorized person than an attacker try to crack it, in our example i will show how to use Thc hydra to pergorm the desired task.
Download thc hydra than use command prompt
C:\Documents and Settings\user\Desktop>hydraAfter that Type "hydra -L userslist.txt -P passlist.txt xxx.xxx.xxx.xxx ftp" and press
enter.
enter.
In our case hydra -L wordlist.txt -P passlist.txt 192.168.1.1 ftp and press enter.